Ad Over 1000 Companies Trust Netsparker With Their Web Application Vulnerability Testing. It is an authorized attempt.
Penetration testing is a combination of techniques that considers various issues of the systems and tests analyzes and gives solutions.
. Here the wrongdoer gathers the maximum amount of. Ad Take your cloud skills to the next level. Information Gathering Threat Modeling. Introduction Penetration testing is a process of validating the impact of specific security vulnerabilities or flawed processes.
Lets Discuss every Phase of a Penetration Testing- a Reconnaissance Coming up with The first part is coming up with. These phases are vital in implementing a. RedTeam Securitys penetration testing methodology assesses the targeted Internet-facing and internal systems using a multi-layered approach. Penetration testing methodologies are important for selecting the right assessment techniques because the selection of test cases and threat models can influence security assessments.
Get 40 off before its gone. Manual Automated Penetration Testing. Unlock The Free Webinar Today. Penetration Testing Methodologies 1.
Learn The Nuances of Cloud Penetration Testing. Penetration testing or pen testing is a simulation of a cyberattack that tests a computer system network or application for security weaknesses. Recon The recon phase consists in. PTES defines a baseline for the minimum that is required for a basic pentest as well as several.
Proof Of Exploit Technology Eliminates The Need For Manual False Positive Verification. Ad Gain a Complete Understanding of Exploitable Vulnerabilities in Your Environment. Ad Comprehensive Web App Infrastructure and Network Testing. Ad Over 1000 Companies Trust Netsparker With Their Web Application Vulnerability Testing.
Combining the benefits of manual and automation testing ensures effective monitored and precise penetration testing. Learn The Nuances of Cloud Penetration Testing. These tests rely on a mix of. Ad Gain a Complete Understanding of Exploitable Vulnerabilities in Your Environment.
Ad Comprehensive Web App Infrastructure and Network Testing. Penetration testing is a method for assessing the security level of a companys software and technology. It is based on a structured procedure that performs. Our Penetration Testing methodology is broken down into six distinct phases.
These cover everything related to a penetration. Proof Of Exploit Technology Eliminates The Need For Manual False Positive Verification. A penetration test is based on a four-phase methodology which is a cyclic process. The OSSTMM framework one of the most recognized standards in.
Stamp out security weaknesses. Recon Mapping Discovery Exploitation. There are seven main steps involved in a successful penetration testing process. The penetration testing execution standard consists of seven phases.
Initial Scoping Reconnaissance Assessment Reporting Presentation and Remediation. Deal valid for individual annual plans. The penetration testing execution standard consists of seven 7 main sections. Unlock The Free Webinar Today.
Stay ahead of the hackers and protect your business-critical data today. Companies hire software and technology experts who attempt to. Here are 5 penetration testing methodologies and standards that will guarantee a return on your investment. Stay ahead of the hackers and protect your business-critical data today.
Stamp out security weaknesses. High Level Organization of the Standard. Penetration Testing Methodology.

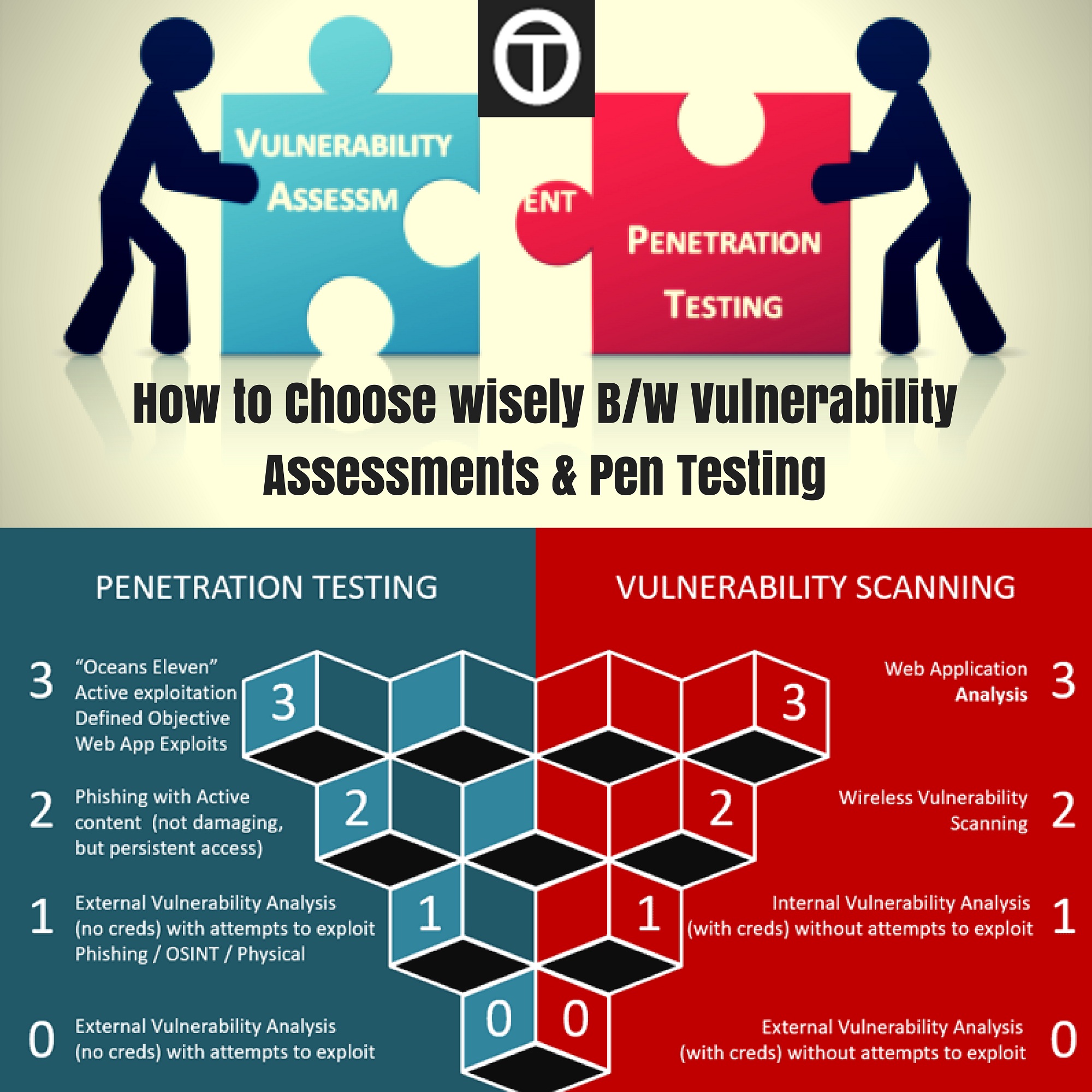
How To Choose Wisely B W Vulnerability Assessments Pen Testing Vulnerability Internet Usage Choose Wisely

Best Methodology By Entersoft For Web App Security Testing Web Application Mobile Application Web App



